Re)started reading "Writing Security Code". Seems a very useful book.
Also now become a regular vistor to www.securityfocus.com and have registered to the mailing lists like BugTraq.
Learning is still interesting....
i am learning the basics.......!
Friday, November 09, 2007
Friday, June 22, 2007
Tools
I should be familiar with tools more ---
Here is a nice way to get dhcp message dump using tcpdump tool
http://www.mavetju.org/unix/dhcpdump-man.php
Here is a nice way to get dhcp message dump using tcpdump tool
http://www.mavetju.org/unix/dhcpdump-man.php
Friday, March 02, 2007
Setupapi.log - very useful
To debug driver installations setupapi.log is very useful. Its present in WINNT folder.
If any probs in NDIS driver installations at site, i ask support engineers to increase loglevel of setupapi and request the logs. Its easy to narrow down the issue.
To increase loglevel of setupapi.log
1. If the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup registry subkey does not contain a LogLevel entry, create one as a new REG_DWORD value.
2. Set the value of the LogLevel entry to the 0x2000FFFF.
If any probs in NDIS driver installations at site, i ask support engineers to increase loglevel of setupapi and request the logs. Its easy to narrow down the issue.
To increase loglevel of setupapi.log
1. If the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup registry subkey does not contain a LogLevel entry, create one as a new REG_DWORD value.
2. Set the value of the LogLevel entry to the 0x2000FFFF.
Thursday, February 15, 2007
Adding certificate to "local computer"
I was trying to add certificate to local computer instead of user profile.. Found only after some investigation. Sharing the results.
1. Launch mmc.exe
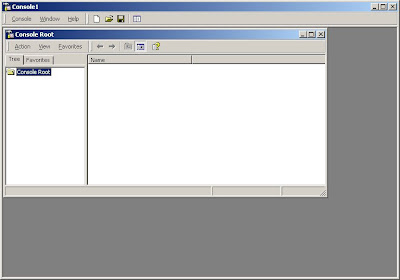 2. "Add Remove Snap-In" from Console
2. "Add Remove Snap-In" from Console
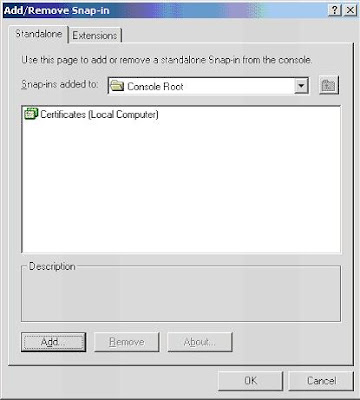
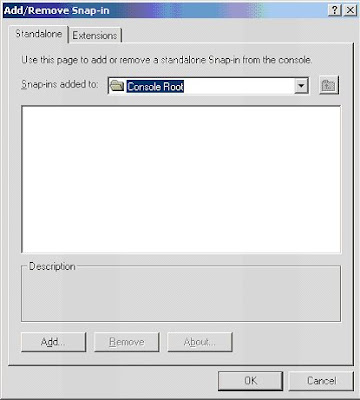 3. "Add"
3. "Add"
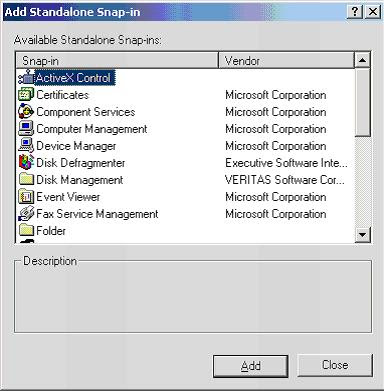 4. Select "certificates" and then "Computer account"
4. Select "certificates" and then "Computer account"
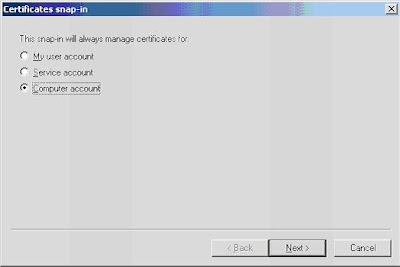 5. Finish
5. Finish
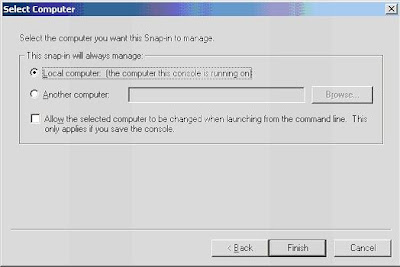 6. Managing certificates will be now possible!
6. Managing certificates will be now possible!
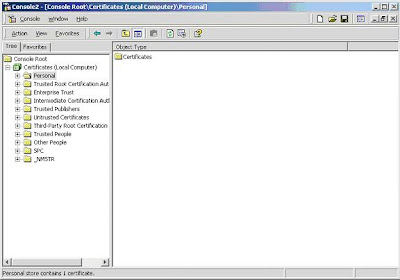 7. "import" certificates.
7. "import" certificates.
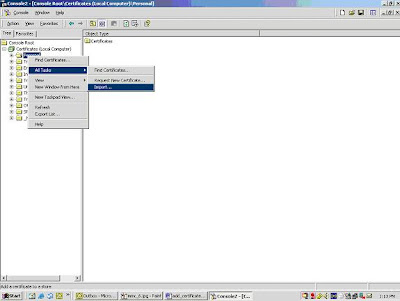 8. Wizard for installing certificate will be launched .., using that we will be able to select certificate and install
8. Wizard for installing certificate will be launched .., using that we will be able to select certificate and install

1. Launch mmc.exe
 2. "Add Remove Snap-In" from Console
2. "Add Remove Snap-In" from Console 3. "Add"
3. "Add" 4. Select "certificates" and then "Computer account"
4. Select "certificates" and then "Computer account" 5. Finish
5. Finish 6. Managing certificates will be now possible!
6. Managing certificates will be now possible!
 7. "import" certificates.
7. "import" certificates. 8. Wizard for installing certificate will be launched .., using that we will be able to select certificate and install
8. Wizard for installing certificate will be launched .., using that we will be able to select certificate and install
Tuesday, February 13, 2007
Forrestor SSLVPN report
Analysis of the SSL VPN solutions available in the market - Report in pdf
Advantages of Nortel lies in:
1. Dual solutions - IPSec and SSLVPN in one box
2. Good clustering and fail-over capabilities
Advantages of Nortel lies in:
1. Dual solutions - IPSec and SSLVPN in one box
2. Good clustering and fail-over capabilities
Thursday, February 01, 2007
Select certificate
This article is a good reference - How To Select Client Certificate in WinInet
HTTPSendRequest will fail with error code - ERROR_INTERNET_CLIENT_AUTH_CERT_NEEDED (12044) if it needs a valid client certificate.
When the error comes: 1. Open the Microsoft certificate store - CertOpenSore
2. Find the certificate using - CertFindCertificateInStore() and get the CERT_CONTEXT
3. Use InternetSetOption with parameter - INTERNET_OPTION_CLIENT_CERT_CONTEXT. LPVOID). lpBuffer parameter should point to CERT_CONTEXT structure.
The KB article provided in the link was very much helpful to me.
HTTPSendRequest will fail with error code - ERROR_INTERNET_CLIENT_AUTH_CERT_NEEDED (12044) if it needs a valid client certificate.
When the error comes: 1. Open the Microsoft certificate store - CertOpenSore
2. Find the certificate using - CertFindCertificateInStore() and get the CERT_CONTEXT
3. Use InternetSetOption with parameter - INTERNET_OPTION_CLIENT_CERT_CONTEXT. LPVOID). lpBuffer parameter should point to CERT_CONTEXT structure.
The KB article provided in the link was very much helpful to me.
Tuesday, January 30, 2007
Multiple Stage Fragmentation
 Hi.., we had a discussion on how multiple stage fragmentation works..
Hi.., we had a discussion on how multiple stage fragmentation works..First question was:1. where does the re-assembly of fragmented packets occur ?
Consider communication btw Device A and Device B. The IP Datagram is 12000bytes. The first link has a MTU 3300 bytes, the second link has MTU 1300 bytes and the third and final link has MTU 1300 bytes.
When the packet goes thru the first link it is fragmented to 3300 bytes, and the fragmented packets are again fragmented to 1300 bytes while passing through second link. Although the third link has MTU 3300 bytes, it is not assembled back. It is re-assembled only at the receiver Device B.
2. How does the re-assembly occurs at the receiving end ?
Every datagram whether fragmented or not is given an Identification number by the Source of the datagram - in this case Device A. This is a random number. The fragments of the datagram are identified using this number- as it is unique. Even if multiple fragmentation occurs this identification number does not change. So Device B can identify all fragments of a datagram using this.
Also where the fragments fit in is specified using "offset field" and not with an "index number". So the receiving end has no problem in assembling the packets.
Sunday, January 21, 2007
RSA SecurId - two factor authentication
Currently working on RSA SecurId Authentication.
RSA SecurId is a popular two factor authentication mechanism.
For successful authentication, not only you need what you KNOW ( say a PASSWORD), but also what you HAVE ( a SecurId device which generates TOKEN every 60s).
The TOKEN is generated by Device and also RSA Server from the TIME and also the SEED ( say a Unique number for that Device Serial Number)
RSA SecurId is a popular two factor authentication mechanism.
For successful authentication, not only you need what you KNOW ( say a PASSWORD), but also what you HAVE ( a SecurId device which generates TOKEN every 60s).
The TOKEN is generated by Device and also RSA Server from the TIME and also the SEED ( say a Unique number for that Device Serial Number)
Monday, January 01, 2007
Why SOCKS?
This link "Why SOCKS?" has the answer>
Just wanted to comment on the "Application-independent proxy" aspect. Once SOCKS client gets authenticated with SOCKS Proxy Server, and communication channel is established it can relay any Application data type. No extra code is required.
This is because SOCKS client works between Application layer and Transport layer, and it does not do anything which is application specific. Based on the encryption and encapsulation techniques selected, it will encode the data and send accordingly!
Just wanted to comment on the "Application-independent proxy" aspect. Once SOCKS client gets authenticated with SOCKS Proxy Server, and communication channel is established it can relay any Application data type. No extra code is required.
This is because SOCKS client works between Application layer and Transport layer, and it does not do anything which is application specific. Based on the encryption and encapsulation techniques selected, it will encode the data and send accordingly!
Subscribe to:
Comments (Atom)
I visit
About Me
- Anoop G
- Predictably Unpredicatble, lazy, careless, sincere, honest, caring, Trouble maker, emotional, likeable